If you're looking to boost your online privacy, it's likely you've read that using one of the best VPN services is the best way to go about it. We would know – at TechRadar we're always writing about VPNs, and recommend our favorite providers.
However, security firm INVISV is arguing that a VPN isn't the right tool from a privacy and security standpoint.
This is why it has developed its INVISV Relay software that, it claims, is a better option for protecting users' data.
But, how do multi-party relays (MPRs) work in practice? And, can it really fully replace your virtual private network?
The problem around trust
"We're challenging something basic in that space: that to protect our privacy we need to hand over our data to some specific company (like a VPN provider) who will supposedly protect us," said INVISV co-founder Barath Raghavan.
According to Raghavan and his business partner Paul Schmitt, the issue lies on the software infrastructure that implies a degree of trust between users and software providers. The same concept also applies to companies behind the best antivirus software or secure email services, for example.
They also believe that independent VPN audits - a growing practice across the privacy sector - cannot fully address this security flaw either, as these still rely on a certain degree of trust from users. Whereas, according to INVISV, it's better to put the protections directly into the software architecture.
"There's so many of these kinds of third parties that they say 'trust us, send us your data and we will fix your security or privacy problem,'" Raghavan told TechRadar. "This is not really the right design for privacy."
How do MPRs work?
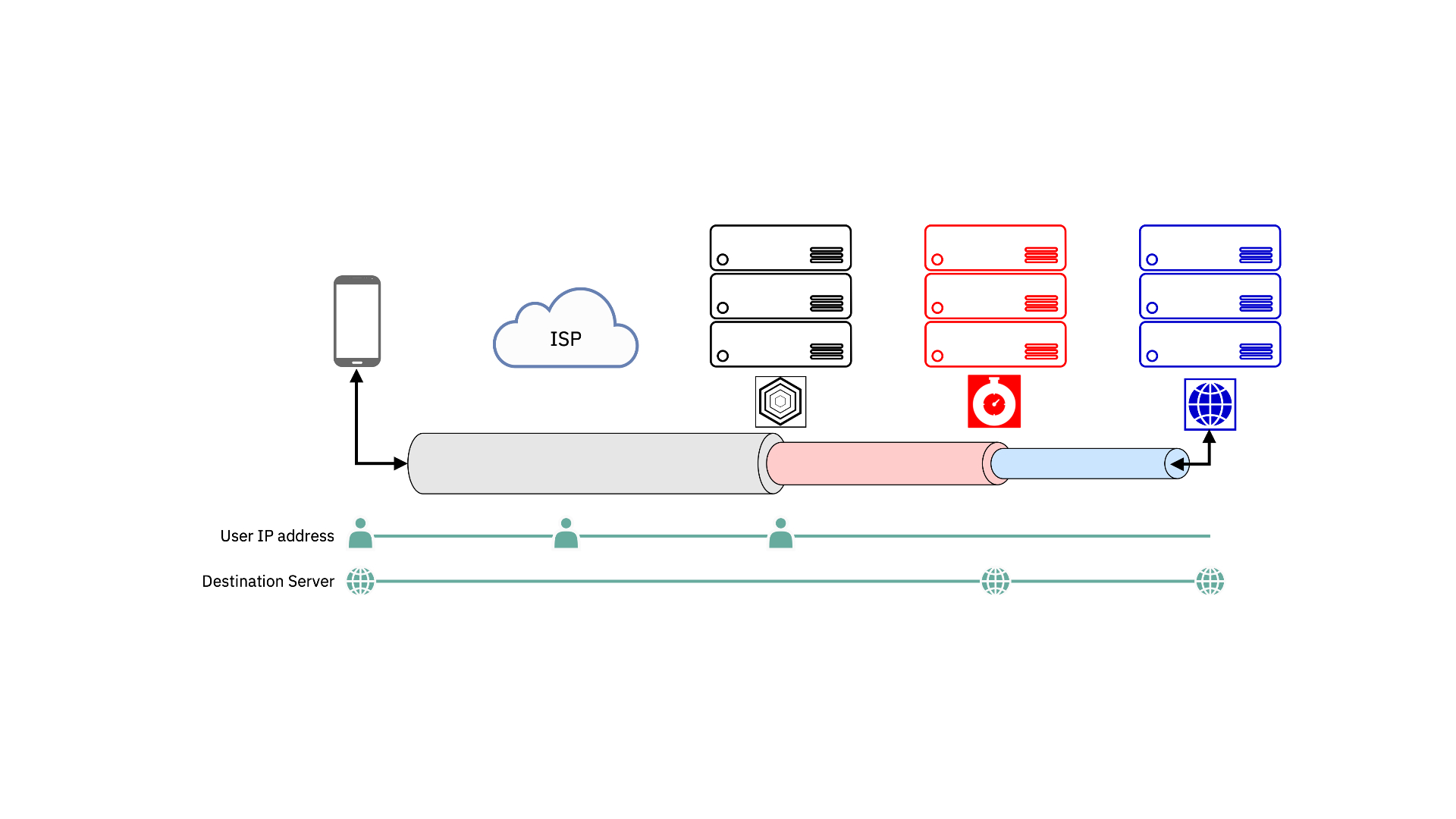
Available only on Android devices, INVISV Relay is an MPR, designed on the principle that none of the parties involved can see in full any user-linkable data. However, INVISV Relay certainly isn't the first MPR around. Apple Private Relay is indeed a very similar tool available for iOS.
Both these apps are built on a privacy design formulated by US computer scientist David Chaum in the 1980s – something known as the Decoupling Principle.
Here, the data traffic travels across two separate servers run by two distinct organizations. Theoretically, none of the party involved can see the full string of information, meaning that it won't be possible associate users' identity with their activities.
Tor browser, for example, is built on the same premise – described as "onion routing". However, being a free software and generally using three layer of encryption as a default, Tor lacks the level of performance that most mobile users might require.
"What we have done has been creating something that has the right privacy principle but is fast," said Raghavan, promising that INVISV Relay can run as fast as your normal browsing connection.
For doing so, the service uses one of the best CDN networks around, Fastly, as it implements the encryption protocol known as IETF Masque that combines TLS-encrypted HTTPS connections with reliable and fast performance. It's also open-source, meaning that anyone can check out the network for vulnerabilities.
Your data will leave your device passing through a TLS-encrypted tunnel to reach the first server run by INVISV. As the company explained to us, this server will be able to see just a stream of encrypted data traveling from your IP address to the next hop, the one operated by Fastly.
At this point, Fastly will decrypt your data in transit but it will be able to see this as coming from the INVISV server instead of a specific user. It will then route your information to your final destination.
Can MPRs replace VPNs?
So, MPRs appear to have the potential to better secure your online data without the worry that the companies involved might store or leak your sensitive information.
However, there are still a wide range of use cases where opting for a VPN is the better bet.
First of all, both INVISV Relay and Apple Private Relay are available for mobile devices only at the moment – Android and iOS, respectively. This means that a VPN is still the best solution to browse the web anonymously on your laptop or PC while enjoying fast connection speeds.

Also, a key limitation of any MPRs is that they are not designed for those looking to change their IP address. So, if you want to bypass any kind of online restrictions – be it your school or workspace firewall or your government's online censorship – you still need a good VPN to do so.
One of the most popular VPN uses isn't even to do with security - it's about streaming. By connecting to various servers around the world, VPN users can spoof their virtual location and access streaming content that's unavailable or prohibitively expensive in their own region. Since MPRs don't affect your virtual location, this is off the table.
"What we're really trying to point out is that there's just a different way to protect privacy that people should be doing," explains Raghavan. "We're trying to provide something that's practical for the average user, that will just improve their privacy without the need to rely on any promises from anybody."
So, for those simply looking to protect their browsing and decouple their identity from their browsing habits, an MPR is a good choice. However, if you're looking for any of the other benefits traditionally offered by VPNs, an MPR can't deliver.

No comments:
Post a Comment