Google has clapped back in tremendous fashion at Epic Games, which earlier this month decided to make the phenomenally popular Fortnite available for Android via its own website instead of Google’s Play Store. Unfortunately, the installer had a phenomenally dangerous security flaw in it that would allow a malicious actor to essentially install any software they wanted. Google wasted exactly zero time pointing out this egregious mistake.
By way of a short explanation why this was even happening, Epic explained when it announced its plan that it would be good to have “competition among software sources on Android,” and that the best would “succeed based on merit.” Everyone of course understood that what he meant was that Epic didn’t want to share the revenue from its cash cow with Google, which takes 30 percent of in-app purchases.
Many warned that this was a security risk for several reasons, for example that users would have to enable app installations from unknown sources — something most users have no reason to do. And the Play Store has other protections and features, visible and otherwise, that are useful for users.
Google, understandably, was not amused with Epic’s play, which no doubt played a part in the decision to scrutinize the download and installation process — though I’m sure the safety of its users was also a motivating factor. And wouldn’t you know it, they found a whopper right off the bat.
In a thread posted a week after the Fortnite downloader went live, a Google engineer by the name of Edward explained that the installer basically would allow an attacker to install anything they want using it.
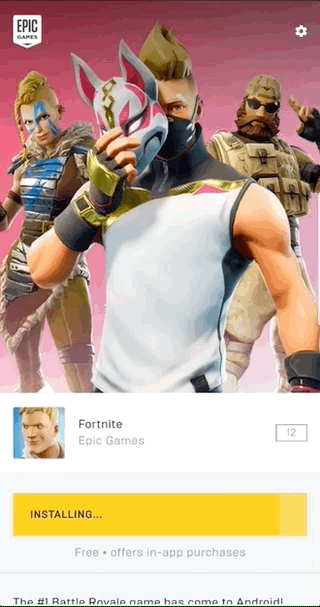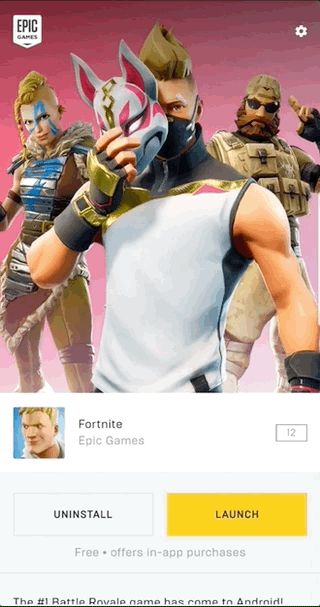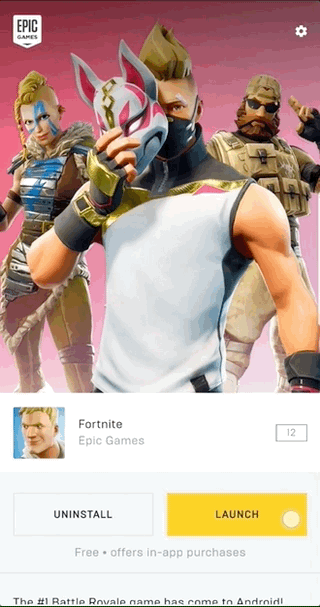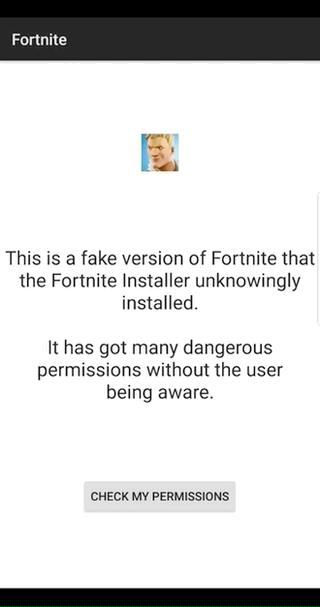 The Fortnite installer basically downloads an APK (the package for Android apps), stores it locally, then launches it. But because it was stored on shared external storage, an bad guy could swap in a new file for it to launch, in what’s called a “man in the disk” attack.
The Fortnite installer basically downloads an APK (the package for Android apps), stores it locally, then launches it. But because it was stored on shared external storage, an bad guy could swap in a new file for it to launch, in what’s called a “man in the disk” attack.
And because the installer only checked that the name of the APK is right, as long as the attacker’s file is called “com.epicgames.fortnite,” it would be installed! Silently, and with lots of extra permissions too, if they want, because of how the unknown sources installation policies work. Not good!
Edward pointed out this could be fixed easily and in a magnificently low-key bit of shade-throwing helpfully linked to a page on the Android developer site outlining the basic feature Epic should have used.
To Epic’s credit, its engineers jumped on the problem immediately and had a fix in the works by that very afternoon and deployed by the next one. Epic InfoSec then requested Google to wait 90 days before publishing the information.
As you can see, Google was not feeling generous. One week later (that’s today) and the flaw has been published on the Google Issue Tracker site in all its… well, not glory exactly. Really, the opposite of glory. This seems to have been Google’s way of warning any would-be Play Store mutineers that they would not be given gentle handling.
Epic Games CEO Tim Sweeney was likewise unamused. In a comment provided to Android Central — which, by the way, predicted that this exact thing would happen — he took the company to task for its “irresponsible” decision to “endanger users.”
Epic genuinely appreciated Google’s effort to perform an in-depth security audit of Fortnite immediately following our release on Android, and share the results with Epic so we could speedily issue an update to fix the flaw they discovered.
However, it was irresponsible of Google to publicly disclose the technical details of the flaw so quickly, while many installations had not yet been updated and were still vulnerable.
An Epic security engineer, at my urging, requested Google delay public disclosure for the typical 90 days to allow time for the update to be more widely installed. Google refused. You can read it all at https://ift.tt/2PBk1Mg
Google’s security analysis efforts are appreciated and benefit the Android platform, however a company as powerful as Google should practice more responsible disclosure timing than this, and not endanger users in the course of its counter-PR efforts against Epic’s distribution of Fortnite outside of Google Play.
Indeed, companies really should try not to endanger their users for selfish reasons.
No comments:
Post a Comment